Resource Posts In Category
Apple a Monopolist? Only in Microsoft-Think
I recently read another positive article about Apple in Computerworld, this one covering Apple's 5 Biggest Moments in 2008. Unlike some other Apple coverage in Computerworld, this one was largely a yawn, but don't you know that most of the comments (as usual) were from Windows partisans who were simply angry that Apple was given any positive coverage at all!
Recently, that seems to be the standard for virtually any online article that has something nice to say about Apple. Rather than commenting on the substance of the article, some anti-Apple type will immediately start dissing the company in a totally ignorant and offensive manner. Sometimes, such drivel will be met with commenters defending Apple, but quite often it merely attracts other Apple hecklers.
The Computerworld article cited above was no different, but there was one comment from a guy who, though claiming to have some positive feelings about Apple, levels a charge that comes straight from the Microsoft propaganda machine. This propaganda only started a few years ago, when Apple began to have success with non-computer products like iTunes, the iPod, and now the iPhone. Microsoft loved to spread the word that Apple's products were all "closed," while Microsoft's were "open," and many listeners, without actually thinking about this illogical line of thinking, bought the propaganda and are now spreading it themselves.
So it was with this writer on Computerworld, who stated:
Ok, I have to do some flaming here. Apple is a VERY innovative company. I even own some Apple creations. However; not everything Apple does is golden and I think that was minimized by the article. They are the most controlling monopolistic protectionist company in electronics and media. I am not a Microsoft fan, but I am thinking even M$ worships at the alter of Apple's ability to monopolize. If M$ tried half the things Apple flaunts they would be in courts all over the world - again.
These OS revisions... Bunk. Usually not more then a service pack. True Leopard was an advancement, but with only a .x revision? Whatever. It is a way for Apple to make money that has not sunk in with the M$ lot yet. Yearly $99 updates... Much better then 4-5 year complete revisions overall for the company's bottom line. Apple's UNIX flavor is very friendly to these updates too, unlike the M$ monster.
AppStore. Distribution limited to Apple's discretion? Hefty profit sharing with Apple... There are pro's and con's but MONOPOLY is what it comes down to. The word never came up in the article but that is what it amounts to. Think if MS tried to do that? Or RIM or Palm, etc.
iTunes. True great functionality, but at the same time I have complaints. I want to buy 20 songs at once - still can't REALLY do that. (i.e. Fill a cart and then buy) How about the Apple updater that wants you to install all kinds of invasive apps all the time? It IS very invasive too - the fact that it bloats your OS by running half a dozen services at all times is nuts.
iPods/iPhones. Require iTunes for support... Only work with iTunes to date... MONOPOLY?
I just couldn't let this challenge go unanswered, so I didn't. The following is what I published in response on Computerworld. In a nutshell, it explains why this guy's line of reasoning is bunk, and why, no matter how much Microsoft would like folks to think so, Apple is absolutely not a monopolist in any sense of the term.
Confusion over the term "monopoly"
First up in the comments to this article there was the guy who asserted that Microsoft isn't a monopolist even though they have been convicted as one. They still have a legally defined monopoly on corporate desktops, as well as of office productivity software.
Then there's this guy who thinks Apple has a monopoly just because it owns and runs the iTunes store or the AppStore. This is MicrosoftThink at its greatest. Let's see...
Apple produces iTunes. Apple makes iPods. Apple makes iPhones. Apple makes Macs. Etc.
Apple doesn't let anyone else run the iTunes or Appstores, nor do they let other companies produce iPods, iPhones, or Macs.
Microsoft-Think says this is BAD. Why? Because MS is a software company that doesn't make hardware (well, except for Xbox and they're iPod-wannabe), but lets lots of hardware companies license their OS (with lots of strings attached, of course). This has been a very successful model for MS, but is it an appropriate model to use as the basis for looking at Apple?
Hardly.
Apple has always (well, except for a short period when they were desperate) maintained that ensuring quality products requires that they produce both the hardware and software components. There's nothing whatsoever wrong with this model. In fact, this is the model for nearly all the rest of the industrial market. The MS model is a historical accident resulting from IBM's dumb mistake in letting them provide the software for their PC, and then letting other companies clone said PC.
Consider:Toyota makes cars. Toyota makes trucks.Does Toyota let anyone else make Toyota cars or trucks? Of course not.Does that make Toyota a monopoly? It's really silly to ask.
Or...
General Electric makes refrigerators, microwaves, dishwashers, radios, etc.Does GE license the blueprints for these products to other companies?Like I said, what a silly question!
Or...
Amazon.com runs an online store selling books and thousands of other products, sort of an online department store like Macys.While Amazon lets other sellers market their wares on the Amazon store, they don't let anyone else use the intellectual property they developed to build the store, populate it with goods, process transactions, handle customers, etc. No one but Amazon can run the Amazon store.
In much the same way, Apple lets musicians and software developers market their goods on their iTunes stores. Just like Amazon, Apple screens products and suppliers to make sure their products meet the company's standards.
Or finally...
Another parallel to consider re: the store concept is the brick-and-mortar model. Who do you think buys products for Macys? If you think it's anyone but a Macy's employee, you're seriously out of touch. Of course Macy's buys their own products, and they choose only those that meet Macy's standards.
Why? Well, because it's a Macy's store!
There's nothing at all unusual in this, and if you think there is, you're simply living in a Microsoft-Think universe.
So, learn what a monopoly is, and what it isn't, before you start throwing that term around.
Microsoft IT Shops Upset At Apple’s “Patch Process”
This is clearly a case of limited-brain humans thinking that something different is something bad. Also a bit of Microsoft-minded FUD here, with statements about Mac OS X's "aging code base" (huh?) and Microsoft being "way ahead" of Apple in its security-patching (huh?).
Why should a company like Apple, which has never had even a minor security incident affecting its users, follow the lead of a company like Microsoft, which defined the way to Not build a secure operating system?
Monopoly Charge Against Apple Signals Rising Respect For Mac OS X
It's amazing to me how strongly the readers of Computerworld agree with the monopoly charge and disagree with the views of those, like me, who believe Psystar is just frustrated at not being able to use Mac OS X on its hardware. Apple a monopoly? Hardly. But, as I said in my comment on Computerworld, it may seem so to those who think the Microsoft model of computing is both inevitable and superior to the Apple one:
Let's face it, the whole paradigm of computing is unprecedented in the history of manufacturing. And it's only... what... 30 years old at best? During that time, the two competing models that have emerged are:
- Make operating system software and convince hardware makers to use your product (the Microsoft model), or
- Make the computer hardware as well as the operating system needed to run it (the Apple model)
Obviously, the former has had much more success in the marketplace. But that doesn't mean it's the better model. Why? Well, for one thing, in this case the market didn't really make the decision... IBM did.
IBM was already a monopoly when it started making personal computers, and Microsoft just happened to be the lucky company chosen to make (or rather, buy) the operating system to run on it. That IBM chose Microsoft had much more to do with the sales savvy of Bill Gates than about the quality of their software.
Once Microsoft was in the door with IBM's PC, which was destined to dominate the business market because of IBM's existing standing in the corporate world, that market was simply theirs to lose. Since Microsoft never made hardware to begin with, they only stood to benefit when the IBM "clone" market developed. IBM protested, if you'll remember, but ultimately, since they'd published the specs already, there wasn't anything they could do about it.
Given this actual history, it's clear that Microsoft no more created the model that ultimately gave them a monopoly on corporate desktops than the market made a decision to adopt that model. It was just a fortuitous circumstance for Microsoft, and a reflection of the fact that their business model was in making software alone (until the Xbox and Zune).
On the other hand, Apple was a hardware maker that also made the operating system to run it. With only one brief period, the company has persisted with that model, and I believe they honestly think it's the only way to make truly great computers.
The issue today is that Mac OS X is becoming more popular, and other companies would like a piece of the action. That's well and good, but since Mac OS X is an Apple creation, they are in no way obliged to license it to others. It's like copying machines... Xerox created the market and the hardware, but ultimately other companies reverse-engineered it and made their own versions. Xerox was then forced to compete with other copying machines.
If anyone wants to compete with Apple's OS X, they'll have to build not just a hardware clone, but more importantly a software clone as well.
Because of the complexity and astounding sophistication of Mac OS X and its universe of frameworks, it would be very hard to clone. But ultimately, that's where the competition has to take place. Unless Apple agrees, they are in no way obliged to sell, lease, or share their intellectual capital with any other company.
That doesn't constitute a monopoly, folks. It just constitutes excellent product development and excellent engineering. It has nothing to do with monopoly at all, since there are plenty of competing computers on the market, and in fact Apple has a small minority share of that market.
Sadly, so many people simply forget history, or make up their own to suit their beliefs. Sad, and scary, too.
Phishing and Safari (Part 2): A Sheep in Wolf’s Clothing
And to think I used to like Consumer Reports!
They keep writing me to "come back" and resubscribe, but I've told them that won't happen until they become objective and truly knowledgeable about the Mac... at least as knowledgeable as they are about Windows PCs.
And now, it turns out they're recommending that Mac users "dump Safari," which just happens to be the best web browser on the Mac platform. Oh, and since this article also appears on ZDNet, while other industry journals gave it little play, I begin to conclude that ZDNet is a rats nest of Microsoft zealots.
So, here's the little note I left them today about their latest phishing/Safari scare tactic:
There is nothing in common between phishing and viruses, adware, spyware, or other malware. Phishing is just an old-fashioned scam dressed up in new HTML clothing. Consumers need to be educated about it, and no anti-phishing technology is going to save them. For one thing, most phishing schemes come to consumers through their email client, not their browsers.
Oh, and 6 or 7 years ago, why didn't Consumer Reports advise Windows users to ditch IE? That would have been the single best way for them to avoid Internet malware, but I never heard them do such a thing. The phishing problem pales in comparison to the security nightmares we experienced after IE6 was released (and before SP2), and which millions of Windows users continue to experience today. Active/X is the most dangerous technology out there as far as security is concerned, but is MS being pressured to remove it from IE?
Unfortunately, I don't think we've heard the last of this... At least, until Apple goes ahead and joins the other browsers in adding "anti-phishing technology" to Safari. Like I noted above, it really makes a lot more sense to add this capability to users' mail clients, since phishing is just a form of junk mail in the end.
Phishing and Safari (Part 1): A Sheep in Wolf’s Clothing
There has lately been a rash of articles about how "insecure" Safari is because it has no anti-phishing mechanism. Frankly, I think this is a bunch of hogwash. It's an attempt to show how lax Apple is about security, and, by implication, how great Microsoft is.
It's not that I don't think phishing is a serious problem... I do! It's just that phishing is not a security issue, which is how the anti-Apple, pro-Microsoft (and pro-Firefox) zealots are trying to portray it.
Here's the comment I left on ZDNet's site about this article, dated 7/23/08:
Phishing scams are very bad, but they are not the same as viruses or malware that gets installed on your operating system. Not even in the same category. They are simply a sophisticated con, and unfortunately there are a lot of naive, clueless web users who will click on any link they're offered. Then again, I know people who are so paranoid they won't click on any link in an email at all... even if it comes from a trusted source (like a friend). I'm not at all convinced that anti-phishing software will work any better than junk-mail filters have, though I understand the need to try.
All you guys who are so hot to jump on Apple need to at least know what you're talking about. Though the companies who make money on security vulnerabilities like to lump phishing in with "security" flaws, in my opinion they aren't. Why? Because they pose no threat to the integrity of your computer or to your network.
Later, in reply to a reader who thought I was kidding with this opinion, I wrote:
Of course it's bothersome... on the same plane as the scum who trick old ladies out of their social security checks by conning them into some phony investment.
Phishing is more insidious, but if you have an ounce of common sense, it's easily avoided.
Not so with viruses and spyware, which can invade your system without any action on your part... not even clicking on a link. If following a link loads a virus, that's not phishing, defined as [blockquote] the activity of defrauding an online account holder of financial information by posing as a legitimate company[/blockquote].
My point is, phishing is not so much a security liability as it is a privacy issue... Phishing amounts to identity theft.
I'm not arguing that phishing isn't a serious concern that needs to be addressed. But I'm saying it's not a security issues in that it doesn't install software on your system, invade your network, or propagate itself to others.
I am arguing that it's more like spam, which is likewise a serious problem that can lead individuals to dangerous websites or tempt them into bad decisions. Like spam, I'm doubtful that any software solution to eradicate phishing is possible.
In this light, the urgency to correct a phishing vulnerability is much lower than that to correct a security vulnerability, and the fact that such a vulnerability exists should not alarm users to the same degree.
Turns out this "phishing" scam isn't over with the iPhone or Safari. See more of my ranting in Part 2 of this topic.
Forrester Believes Apple Will Win in Homes
I do not smoke, but it's obvious that you people do. Please send me a kilo of your best. Apple is a small time player with very limited scope, appeal, and resources. There is an obvious reason for that: the buying public does not feel compelled to support them just to "be different".To which I replied:
You may not smoke, but clearly you have your heard buried in the sand. Your irrational anti-Apple attitude is clearly a product of wishful thinking. My only guess is that you own Microsoft stock, which has been flat for years, while Apple stock has skyrocketed. You tihink $190 a share is high for Apple? Just wait a few more years. It's still not too late to face reality and start to cheer, rather than jeer, the company that's put the fun and excitement back into personal computing, as well as home entertainment.The depth and intensity of the anti-Apple pod-People continues to remind me of the Fascists' attitude toward Jews. These guys think Apple fans are religious, but in reality, they're the ones whose brains are dominated by a cult-like hatred. Kinda scary, but then they're typically cowards who wouldn't make such arguments in person.
Computerworld Publishes “I Hate Macs” By Staffer/Blogger
I hate Macs - Computerworld Blogs
It’s been awhile since I read anything so asinine it got me riled up enough to write about it. I couldn’t believe the guy ranted on for a whole column without offering one shred of evidence or fact for his apparently deep-seated hatred of Apple, Steve Jobs, and all things Mac. This, my friends, is prejudice, pure and simple. How is “prejudice” defined?
PREJUDICE:
preconceived opinion that is not based on reason or actual experience.
Precisely. How such a rant ends up in a technology journal that wants to be taken seriously is beyond me. As a Martian, it’s just one more piece of evidence that you humans are not evolving as we’d hoped you would.
I wrote to Computerworld and to the author’s editor suggesting the writer be canned, and they defended him by saying they wanted to offer an “opposing view” about Apple. Huh? What opposing view? Aren’t “views” published by journalists in national magazines supposed to have some–I don’t know–factual weight behind them? Aren’t “journalists” like this supposed to be “experts” at the things they write about?
Yet how can someone be an expert yet have opinions “not based on reason or actual experience”? If you can stomach it, read the piece for yourself. Here’s a typical sample:
And I hate the products themselves. Overpriced, overhyped and underwhelming. Oh, I forgot, they have such “elegant” design. They just “feel right.” All the stubble-cheeked, pony-tailed, black-clad hipsters in the design department get it, but us dweeby drones doing the real work are just out of touch.
Gag me. I’ve always been a function-over-form guy. I don’t give a rat’s, uh, tail, if my computer is smooth and white and shiny. I just want to crank out the next project.
And don’t give me those phony cost comparisons that try to make the case that, all things considered, Macs are cheaper than PCs in the long run. Just look at the damn price tags. Spin it any way you want, Macs and the other iCrap cost more.
And innovation? My god, take the blinders off. I remember sitting right here several years ago when Apple came out with the great new feature on their iPods called “shuffle.” I couldn’t believe it. Before then, you couldn’t play your songs in random order? I had been doing that for years, literally. But then, I was into MP3s early on — my first music player was a Rio PMP300, one of the very first on the market. I didn’t have to wait for Apple to tell me they were cool. It took them a few years to catch on. Gee, where was the bleeding-edge innovation there?

This guy is so pathetic. Even on my non-professional website here, I fact-check like you wouldn’t believe. It’s one reason why it takes me so long to write an article. I happen to have a working copy of every version of iTunes back to 1.1 for Mac OS X, which came out in 2001. Guess what? It’s got shuffle mode. Of course it’s got shuffle! Only someone trying to find something to criticize would claim that Apple ever considered “shuffle mode” to be its innovative idea. Good grief. He’s probably confusing Apple’s marketing for the iPod Shuffle with the “shuffle” concept. In fact, nearly all of his opinions seem to be in reaction to advertising rather than to careful study of the actual products in question.
But enough of this… It was just so wrong I had to point it out. And I do hope Computerworld puts him back in the mailroom where he clearly belongs.
Microsoft Junkies Spreading “Apple Messed Up The iPhone” FUD
I was so incensed by this posting at InfoWorld, which builds on an earlier one by respected InfoWorld Test Center lead Tom Yager, that I dashed off the following email to InfoWorld, canceling my print subscription and putting a stop to all of their RSS feeds. From what I can see through my 18-year-old son's eyes (we got him an iPhone as a high school graduation present), Apple has hit a bulls-eye with this gadget. Playing with it myself for a few minutes, this cellphone, Palm Pilot, and Blackberry resister suddenly understood the appeal of such devices. You really have to try the iPhone interface to appreciate how amazing and revolutionary it is. Clearly, this Oliver Rist creep is more interested in pushing Microsoft technology than in assessing the relative merits of whatever technologies exist. It's reminiscent of the way guys like this tried to talk the iPod into a hole 6 years ago, and given their dramatic failure at that attempt, this anti-iPhone talk would be sad if it weren't so creepy.
I've sadly watched InfoWorld go slowly downhill in the last year, as its IT coverage moved more and more mainstream and less honest. By "mainstream," I mean coverage that pays homage to where its advertising dollars come from rather than to integrity ("honest journalism") and the needs of its readership.After having been mostly a fan of Tom Yager in recent years, I was appalled at the sensational slant of his article on the iPhone, "iPhone: The $1,975 iPod." That article was of course widely quoted and utilized by others at InfoWorld who it seems are determined to talk the device down. Apple has made clear that it isn't a business device (heck, it doesn't even offer business accounts!)... it's a consumer device. And a good many of Yager's "cons" are based on unreasonable assumptions of performance that neither Apple nor any other "smartphone" provider aim for.
All that has done is made idiots who think everything IT should be for business first and people later mad. Today I got this garbage in my inbox:
WHAT GIVES WINDOWS MOBILE EDGE OVER IPHONEColumnist's corner: Even though Apple messed up the iPhone, Oliver Rist writes, "much of the device's problems aren't technical, but just bad business." Not so for Windows Mobile, which is plagued by troubled technology, including ActiveSync issues, Wi-Fi woes, application incompatibility, and worse, its very own Blue Screen of Death. "Microsoft has all the advantages that count in this space right now," Rist adds in Windows Mobile needs fixing fast. "The company really has the chance to win one based on functionality and capability rather than just marketing." The news beat: Sources say that a beta of Vista SP1 is... ...
The InfoWorld writer who wrote this also calls consumer who buy Apple products "iSheep," saying they're the type who "need an Apple logo tattooed on as many of their belongings as possible." This is a guy who probably never understood the appeal of the iPod, either. Heaven forbid that he'd see the virtue of a Mac. And he's determined to do Microsoft's bidding by spreading FUD about the iPhone while it's still in its infancy. This is honest journalism? He bases his lead premise that "Apple messed up the iPhone" on Tom Yager's own piece of crap.
I don't know if Yager chose his article's headline or not... oddly, it doesn't seem like his style to me. Because it's the headline that made me not want to read the rest of whatever garbage he was peddling in that article. My teenager has an iPhone (high school graduation gift), and I figure I'll form my own impression of it by hands-on use [Update: I've now done this... see intro]. I really don't know how anyone can form a valid impression of a device like the iPhone in the few days Yager had before spouting off. Yes, I was disappointed with the arrangement with AT&T, too, and the requirement to buy a plan will keep me from buying an iPhone--at least in the short-term. But I seriously doubt that this requirement defeats the obvious genius of the device itself, as the headline asserts. After all, in my opinion the whole cellular industry is built on greed... nothing comes for free in that market, that I can tell. Yet I'm sure the FCC required Apple to establish a relationship with one of the existing carriers if they wanted to offer such services in the iPhone.
Not only does Yager's headline make the deal sound outlandishly expensive, it also gives AT&T equal billing with Apple as the device's creator in the subtitle. I've never owned a cellular phone... I still don't see how it could possibly be worth spending so much a month in order to be constantly available... but my wife and son are heavy users. My wife's plan is paid for by her employer, or she wouldn't have one either. But we pay a monthly fee for my son's plan... which was a Cigna plan at about $30 a month. The plan had no data or SMTP and very limited call options. That would be $720 for 2 years. His phone has no web connectivity, no bluetooth, no video, no email, and no music options.
With the iPhone, he not only gets an incredibly cool device with a revolutionary interface, but he also gets web, bluetooth, video, music, email, and potentially much more over time. With a 2-year plan, this will cost $1,440, and he'll be getting unlimited data services, some limited text messaging, video email, and all the wireless capabilities as well. I mean, to me, this sounds like a great deal to anyone who can afford it, and you can't measure the value of actually being able to use the device for those functions rather than fiddling with unworkable wands or teeny thumbpads.
So at the most, Yager and other idiotic price critics who just don't get it could argue that the iPhone is $500 over 2 years. Given what it offers in terms of functionality and ease of use, I really doubt that your average consumer, who doesn't have Microsoft or its XMinions whispering in their ear, is going to think that's very expensive. After all, given what my son has said, he plans to replace his current 60GB iPod with this 8GB iPhone. I was surprised he could make do with such a small capacity, but he seems to think the device's other virtues make it well worthwhile.
And this is just the first model iPhone... remember what the previous such idiots said about the first iPod's price? Sheesh.
I wanted you to know that I'm canceling my RSS feeds and will not be renewing my print subscription.
Regards,
Leland Scott
Latest Performance Tests Make WebKit’s Superiority Hard To Deny (But Some Still Try)
Scribus: An Open Source App for Desktop Publishing
Spread The Word: Al Gore Used Keynote For “Inconvenient Truth”… NOT PP
Renkoo Thinks They Don’t Need Mac Users
Selling Vista: Computerworld Makes This OS X Copy Sound Like Microsoft’s Idea
Computerworld Finds Picky Faults With Mac OS X
Apple, Microsoft and the War Mentality
Slashdot: Apple Accused of “Upsampling” Low-Res Videos for iTunes
InfoWorld’s Editor Backs Yager’s Estimate of Apple’s Enterprise-worthiness
Macs Are Inherently Safer for Data Storage
Laughing at Negative Prognostication About Apple
Tom Yager in MacWorld: An Apple for the enterprise?
- Macs are so expensive
- A PC is a PC; who cares who makes it?
- It's a proprietary platform
- Why invest in OSX when Vista is going to wipe it off the map?
- I can't manage a network of mixed platforms
- OS X Server is unproven in critical, high-availability, and large-scale deployments. It's an enterprise wannabe
- Apple controls the availability of systems, parts, upgrades, and service
- Apple's got a smoke-and-mirrors hack that makes Macs run Windows
- Apple's product line is tiny. All other Intel OEMs focus on choice.
Tom, thank you for tackling these myths so publicly. It's time more people in positions of IT influence did the same.
HyperScope Uses Dojo But Leaves Out Mac Users
Is Apple Being Unfairly Targeted on Environmental Issues?
SecureWorks admits to falsifying MacBook wireless hack - The Unofficial Apple Weblog (TUAW)
Protecting Windows: How PC Malware Became A Way of Life
Article Summary
 This is a very long article that covers several different, but related, topics. If you are interested, but don’t have time to read the entire article, here’s a summary of the main themes, with links to the sections of text that cover them:
This is a very long article that covers several different, but related, topics. If you are interested, but don’t have time to read the entire article, here’s a summary of the main themes, with links to the sections of text that cover them:
- Required Security Awareness Classes Reinforce Windows Monopoly in Federal Agencies.
For the third straight year, I’ve been forced to take online “security awareness” training at my Federal agency that includes modules entirely irrelevant–and in fact, quite insulting–to Macintosh users (myself included). The online training requires the use of Internet Explorer, which doesn’t even exist for Mac OS X and in fact is the weakest possible browser to use from a security perspective. It also reinforces the myth that computer viruses, adware, and malicious email attachments are a problem for all users, when in fact they only are a concern to users of Microsoft Windows. In presenting best practices for improved security, the training says absolutely nothing about the inherent security advantages of switching to Mac OS X or Linux, even though this is an increasingly well known and non-controversial solution. This part of the article describes the online training class and the false assumptions behind it in detail. - IT Managers Are Spreading and Sustaining Myths About the Cause of the Malware Plague.
These myths serve to protect the status quo and their own jobs at the expense of users and corporate IT dollars. None of the following “well known” facts are true, and once you realize that malware is not inevitable–at the intensity Windows users have come to expect–you realize there actually are options that can attack the root cause of the problem.- Windows is the primary target of malware because it’s on 95% of the world’s desktops,
- Malware has worsened because there are so many more hackers now thanks to the Internet, and
- All the hackers attack Windows because it’s the biggest target.
This section of the article describes the history of the malware plague and its actual root causes.
- U.S. IT Management Practices Aren’t Designed for Today’s Fast-Moving Technology Environment.
This part of the article discusses why IT management failed to respond effectively to the disruptive plague of malware in this century, and then presents a long list of proposed “Best Practices” for today’s Information Technology organizations. The primary theme is that IT shops cover roughly two kinds of activity: (1) Operations, and (2) Development. Most IT shops are dominated by Operations managers, whose impulse is to preserve the status quo rather than investigate new technologies and alternatives to current practice. A major thrust of my proposed best practices is that the influence of operations managers in the strategic thinking of IT management needs to be minimized and carefully monitored. More emphasis needs to be accorded to the Development thinkers in the organization, who are likely to be more attuned to important new trends in IT and less resistant to and fearful of change, which is the essence of 21st century technology.
Ah, computer security training. Don’t you just love it? Doesn’t it make you feel secure to know that your alert IT department is on patrol against the evil malware that slinks in and takes the network down every now and then, giving you a free afternoon off? Look at all the resources those wise caretakers have activated to keep you safe!
- Virulent antivirus software, which wakes up and takes over your PC several times a day (always, it seems, just at the moment when you actually needed to type something important).
- Very expensive, enterprise-class desktop-management software that happily recommends to management when you need more RAM, when you’ve downloaded peer-to-peer software contrary to company rules, and when you replaced the antivirus software the company provides with a brand that’s a little easier on your CPU.
- Silent, deadly, expensive, and nosy mail server software that reads your mail and removes files with suspicious-looking extensions, or with suspicious-looking subject lines like “I Love You“, while letting creepy-looking email with subject lines like “You didnt answer deniable antecedent” or “in beef gunk” get through.
- Expensive new security personnel, who get to hire even more expensive security contractors, who go on intrusion-detection rampages once or twice a year, spend lots of money, gum up the network, and make recommendations for the company to spend even more money on security the next year.
- Field trips to Redmond, Washington, to hear what Microsoft has to say for itself, returning with expensive new licenses for Groove and SharePoint Portal Server (why both? why either?), and other security-related software.
- New daily meetings that let everyone involved in protecting the network sit and wring their hands while listening to news about the latest computing vulnerabilities that have been discovered.
- And let’s not forget security training! My favorite! By all means, we need to educate the staff on the proper “code of conduct” for handling company information technology gear. Later in the article, I’ll tell you all about the interesting things I learned this year, which earned me an anonymous certificate for passing a new security test. Yay!
In fact, this article started out as a simple expose on the somewhat insulting online training I just took. But one thought led to another, and soon I was ruminating on the Information Technology organization as a whole, and about the effectiveness and rationality of its response to the troublesome invasion of micro-cyberorganisms of the last 6 or 7 years.
Protecting the network
Who makes decisions about computer security for your organization? Chances are, it’s the same guys who set up your network and desktop computer to begin with. When the plague of computer viruses, worms, and other malware began in earnest, the first instinct of these security Tzars was understandable: Protect!
Protect the investment…
Protect the users…
Protect the network!
And the plague itself, which still ravages our computer systems… was this an event that our wise IT leaders had foreseen? Had they been warning employees about the danger of email, the sanctity of passwords, and the evil of internet downloads prior to the first big virus that struck? If your company’s IT staff is anything like mine, I seriously doubt it. Like everyone else, the IT folks in charge of our computing systems at the office only started paying attention after a high-profile disaster or two. Prior to that, it was business as usual for the IT operations types: “Ignore it until you can’t do so anymore.” A vulgar translation of this “code of conduct” is often used instead: “If it ain’t broke, don’t fix it.”
Unfortunately, the IT Powers-That-Be never moved beyond their initial defensive response. They never actually tried to investigate and treat the underlying cause of the plague. No, after they had finished setting up a shield around the perimeter, investing in enterprise antivirus and spam software, and other easy measures, it’s doubtful that your IT department ever stepped back to ask one simple question: How much of the plague has to do with our reliance on Microsoft Windows? Would we be better off by switching to another platform?
It’s doubtful that the question ever crossed their minds, but even if someone did raise it, someone else was ready with an easy put-down or three:
- It’s only because Windows is on 95% of the world’s desktops.
- It’s only because there are so many more hackers now.
- And all the hackers attack Windows because it’s the biggest target.
At about this time in the Computer Virus Wars, the rallying cry of the typical IT shop transitioned from “Protect the network… users… etc.” to simply:
Protect Windows!
Windows security myths
The “facts” about the root causes of the Virus Wars have been repeated so often in every forum where computer security is discussed—from the evening news to talk shows to internal memos and water-cooler chat—that most people quickly learned to simply shut the question out of their minds. There are so many things humans worry about in 2006, and so many things we wonder about, that the more answers we can actually find, the better. People nowadays cling to firm answers like lifelines, because there’s nothing worse than an unsolved mystery that could have a negative impact on you or your loved ones.
Only problem is, the computer security answers IT gave you are wrong. The rise of computer viruses, email worms, adware, spyware, and indeed the whole category now known as “malware” simply could not have happened without the Microsoft Windows monopoly of both PC’s and web browsing and the way the product’s corporate owners responded to the threat. In fact, the rise of the myth helped prolong the outbreak, and perhaps just made it worse, since it took Microsoft off the hook of responsibility… thus conveniently keeping the company’s consideration of the potentially expensive solutions at a very low priority.
 Even though the IT managers who actually get to make decisions didn’t see this coming, it’s been several years now since some smart, brave (in at least one case, a job was lost) people raised a red flag about the vulnerability of our Microsoft “monoculture” to attack. They warned us that reliance on Microsoft Windows, and the impulse to consolidate an entire organization onto one company’s operating system, was a recipe for disaster. Because no one actually raised this warning beforehand, the folks in the mid-to-late 1990’s who were busily wiping out all competing desktops in their native habitat can perhaps be forgiven for doing so. However, IT leaders today who still don’t recognize the danger—and in fact actively resist or ignore the suggestion by others in their organization to change that policy—are being recklessly negligent with their organization’s IT infrastructure. It’s now generally accepted by knowledgeable, objective security experts that the Microsoft Windows “monoculture” is a key component that let the virus outbreak get so bad and stay around for so long. They strongly encourage organizations to loosen the reins on their “Windows only” desktop policy and allow a healthy “heteroculture” to thrive in their organization’s computer desktop environment.
Even though the IT managers who actually get to make decisions didn’t see this coming, it’s been several years now since some smart, brave (in at least one case, a job was lost) people raised a red flag about the vulnerability of our Microsoft “monoculture” to attack. They warned us that reliance on Microsoft Windows, and the impulse to consolidate an entire organization onto one company’s operating system, was a recipe for disaster. Because no one actually raised this warning beforehand, the folks in the mid-to-late 1990’s who were busily wiping out all competing desktops in their native habitat can perhaps be forgiven for doing so. However, IT leaders today who still don’t recognize the danger—and in fact actively resist or ignore the suggestion by others in their organization to change that policy—are being recklessly negligent with their organization’s IT infrastructure. It’s now generally accepted by knowledgeable, objective security experts that the Microsoft Windows “monoculture” is a key component that let the virus outbreak get so bad and stay around for so long. They strongly encourage organizations to loosen the reins on their “Windows only” desktop policy and allow a healthy “heteroculture” to thrive in their organization’s computer desktop environment.
Full disclosure: I was one of the folks who warned their IT organization about the Windows security problem and urged a change of course several years ago. From a white paper delivered to my CIO in November 2002, this was one of my arguments for allowing Mac OS X into my organization as a supported platform:
Promoting a heterogeneous computing environment is in NNN’s best interest from a security perspective. Mactinoshes continue to be far more resistant to computer viruses than Windows systems. The latest studies show that this is not just a matter of Windows being the dominant desktop operating system, but rather it relates to basic security flaws in Windows.
About a year later, when Cyberinsecurity was released, I provided a copy to my company’s Security Officer. But sadly, both efforts fell on deaf ears, and continue to do so.
1999: The plague begins
The first significant computer virus—probably the first one you and I noticed—was actually a worm. The “Melissa Worm” was introduced in March 1999 and quickly clogged Usenet newsgroups, shutting down a significant number of servers. Melissa spread as a worm in Microsoft Word documents. (Note: Wikipedia now maintains a Timeline of Notable Viruses and Worms from the 1980’s to the present.)
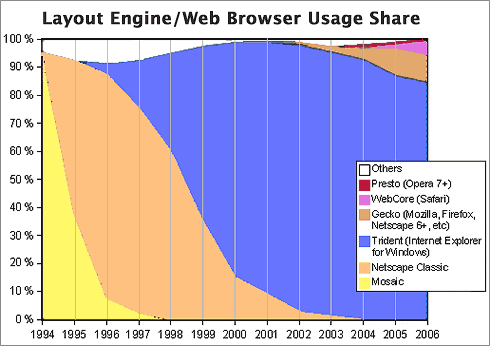
Now, as it so happens, 1999 was also the year when it became clear that Microsoft would win the browser war. In 1998, Internet Explorer had only 35% of the market, still a distant second to Netscape, with about 60%. Yet in 1999, Microsoft’s various illegal actions to extend its desktop monopoly to the browser produced a complete reversal: When history finished counting the year, IE had 65% of the market, and Netscape only 30%. IE’s share rose to over 80% the following year. This development is highly significant to the history of the virus/worm outbreak, yet how many of you have an IT department enlightened enough to help you switch from IE back to Firefox (Netscape’s great grandchild)? The browser war extended the growing desktop-OS monoculture to the web browser, which was the window through which a large chunk of malware was to enter the personal computer.
 You see, by 1994, a year or so before the World Wide Web became widely known through the Mosaic and Netscape browsers, Microsoft had already achieved dominance of the desktop computer market, having a market share of more than 90%. A year later, Windows 95 nailed the lid on the coffin of its only significant competitor, Apple’s Macintosh operating system, which in that year had only about 9% of corporate desktops. Netscape was the only remaining threat to a true computing monoculture, since as the company had recognized, the web browser was going to become the operating system of the future.
You see, by 1994, a year or so before the World Wide Web became widely known through the Mosaic and Netscape browsers, Microsoft had already achieved dominance of the desktop computer market, having a market share of more than 90%. A year later, Windows 95 nailed the lid on the coffin of its only significant competitor, Apple’s Macintosh operating system, which in that year had only about 9% of corporate desktops. Netscape was the only remaining threat to a true computing monoculture, since as the company had recognized, the web browser was going to become the operating system of the future.
Microsoft’s hardball tactics in beating back Netscape led directly to the insecure computer desktops of the 2000 decade by ensuring that viruses written in “Windows DNA” would be easy to disseminate through Internet Explorer’s Active/X layer. Active/X basically let Microsoft’s legions of Visual Basic semi-developers write garbage programs that could run inside IE, and it became a simple matter to write garbage programs as Trojan Horses to infect a Windows PC. Active/X was a heckuva lot easier to write to than Netscape’s cross-platform plug-in API, which gave IE a huge advantage as developers sought to include Windows OS and MS Office functionality directly in the web browser.
A similar strategy was taking place on the server side of the web, as Microsoft’s web server, Internet Information Server (IIS), had similarly magical tie-in’s to everybody’s favorite desktop OS. Fortunately for the business world, the guys in IT who had the job of managing servers were always a little bit brighter than the ones who managed desktops. They understood the virtues of Unix systems, especially in the realm of security. IT managers weren’t willing to fight for Windows at the server end of the business once IIS was revealed to have so many security holes. As a result, Windows, and IIS, never achieved the dominance of the server market that Microsoft hoped for, although you can be sure that the company hasn’t given up on that quest.
The other major avenue for viruses and worms has been Microsoft Office. As noted, Melissa attacked Microsoft Word documents, but this was a fairly unsophisticated tactic compared with the opportunity presented by Microsoft’s email program, Outlook. Companies with Microsoft Exchange servers in the background and Outlook mail clients up front, which by the late 1990’s had become the dominant culture for email in corporate America, presented irresistable targets for hackers.
 Through the web browser, the email program, the word processor, and the web server, the opportunities for cybermischief simply multiplied. Heck, you didn’t even have to be a particularly good programmer to take advantage of all the security holes Microsoft offered, which numbered at least as many as would be needed to fill the Albert Hall (I’m still not sure how many that is).
Through the web browser, the email program, the word processor, and the web server, the opportunities for cybermischief simply multiplied. Heck, you didn’t even have to be a particularly good programmer to take advantage of all the security holes Microsoft offered, which numbered at least as many as would be needed to fill the Albert Hall (I’m still not sure how many that is).
So… the answer to the question of why viruses and worms disproportionately took down Windows servers, networks, and desktops starting in 1999 isn’t that Microsoft was the biggest target… It was because Microsoft Windows was the easiest target.
And the answer to why viruses and worms proliferated so rapidly in the 2000’s and with them the Windows-hacker hordes is simply that hacking Microsoft Windows became a rite of passage on your way to programmer immortality. Why try to attack the really difficult targets in the Unix world, which had already erected mature defenses by the time the Web arrived, when you could wreak havoc for a day or a week by letting your creation loose at another clueless Microsoft-Windows-dominated company? Once everyone was using both Windows and IE, spreading malware became child’s play. You could just put your code in a web page! IE would happily swallow the goodie, and once inside, the host was defenseless.
Which leads me to the next question whose answer has been obscured in myth: Exactly why was the host defenseless? That is, why couldn’t Windows fight off viruses and worms that it encountered? It doesn’t take a physician to know the answer to that one, folks. When you encounter an organism in nature that keeps getting sick when others don’t, it’s a pretty good bet that there’s something wrong with its immune system.
The trusting computer
It’s not commonly known or understood outside of the computer security field that Windows represents a kind of security model called “trusted computing.” Although you’d think this model would have been thoroughly discredited by our collective experience with it over the last decade, it’s a model that Microsoft and its allies still believe in… and still plan to include in their future products such as Windows Vista. Trusted computing has a meaning that’s shifted over the years, but as embodied by Microsoft Windows variants since the beginning of the species, it means that the operating system trusts the software that gets installed on it by default, rather than being suspicious of unknown software by default.
That description is admittedly a simplification, but this debate needs to be simplified so people can understand the difference between Windows and the competition (to the extent that Windows has competition, I’m talking about Mac OS X and Linux). The difference, which clearly explains why Windows is unable to defend itself from attack by viruses and worms, stems from the way Windows handles user accounts, compared with the way Unix-like systems, such as Linux and Mac OS X, handle them. Once you understand this, I think it will be obvious why the virus plague has so lopsidedly affected Windows systems, and it will dispel another of the myths that have been spread around to explain it.
Windows has always been a single-user system, and to do anything meaningful in configuring Windows, you had to be set up as an administrator for the system. If you’ve ever worked at a company that tried to prevent its users from being administrators of their desktop PC’s, you already know how impossible it is. You might as well ask employees to voluntarily replace their personal computer with a dumb terminal. [Update 8/7/06: I think some readers rolled their eyes at this characterization (I saw you!). You must be one of the folks stuck at a company that has more power over its employees than the ones I've worked for in the last 20-odd years. Lucky you! I don't have data on whose experience is more common, but naturally I suspect it's not yours. No matter... this is certainly true for home users ....] And home users are always administrators by default… besides, there’s nothing in the setup of a Windows PC at home that would clearly inform the owner that they had an alternative to setting up their user accounts. (Update 8/7/06: Note to Microsoft fans who take umbrage at this characterization of their favorite operating system: Here’s Microsoft’s own explanation of the User Accounts options in Windows XP Professional.)
The Unix difference: “Don’t trust anyone!”
On Unix systems, which have always been multiuser systems, the system permissions of a Windows administrator are virtually the same as those granted to the “superuser,” or “root” user. In the Unix world, ordinary users grow up living in awe of the person who has root access to the system, since it’s typically only one or two system administrators. Root users can do anything, just as a Windows administrator can.
But here’s the huge difference: A root user can give administrator access to other users, granting them privileges that let them do the things a Windows administrator normally needs to do—system administration, configuration, software installing and testing, etc—but without giving them all the keys to the kingdom. A Unix user with administrator access can’t overwrite most of the key files that hackers like to fool with—passwords, system-level files that maintain the OS, files that establish trusted relationships with other computers in the network, and so on.
 Windows lacks this intermediate-level administrator account, as well as other finer-grained account types, primarily because Windows has always been designed as a single-user system. As a result, software that a Windows user installs is typically running with privileges equivalent to those of a Unix superuser, so it can do anything it wants on their system. A virus or worm that infects a Unix system, on the other hand, can only do damage to that user’s files and to the settings they have access to as a Unix administrator. It can’t touch the system files or the sensitive files that would help a virus replicate itself across the network.
Windows lacks this intermediate-level administrator account, as well as other finer-grained account types, primarily because Windows has always been designed as a single-user system. As a result, software that a Windows user installs is typically running with privileges equivalent to those of a Unix superuser, so it can do anything it wants on their system. A virus or worm that infects a Unix system, on the other hand, can only do damage to that user’s files and to the settings they have access to as a Unix administrator. It can’t touch the system files or the sensitive files that would help a virus replicate itself across the network.
This crucial difference is one of the main ways in which Mac OS X and Linux are inherently more secure than Windows is. On Mac OS X, the root user isn’t even activated by default. Therefore, there’s absolutely no chance that a hacker could log in as root: The root user exists only as a background-system entity until a Mac user deliberately instantiates her, and very few people ever do. I don’t think this is the case on Linux or other Unix OS’s, but it’s one of the things that makes Mac OS X one of the most secure operating systems available today.
There are many other mistakes Microsoft has made in designing its insecure operating system—things it could have learned from the Unix experience if it had wanted to. But this one is the doozy that all by itself puts to rest the notion that Microsoft Windows has been attacked more because people don’t like Microsoft, or because it’s the biggest target, or all the other excuses that have been promulgated.
The security awareness class
In response to the cybersecurity crisis, one of the steps our Nation’s IT cowards leaders have taken across the country is to purchase and customize computer security “training.” Such training is now mandatory in the Federal Government and is widely employed in the private sector. I have been forced to endure it for three years now, and I’ve had to pass a quiz at the end for the last two. As a Macintosh user, I naturally find the training offensive, because so much of it is irrelevant to me. It’s also offensive because it is the byproduct of decisions my organization’s IT management has made over the years that in my view are patently absurd. If the decisions had been mine, I would never have allowed my company to become completely dependent on the technological leadership of a single company, especially not one whose product was so difficult to maintain.
It’s a truism to me, and has been for several years now, that Windows computers should simply not be allowed to connect to the Internet. They are too hard to keep secure. Despite the millions that have been spent at my organization alone, does anybody actually believe that our Windows monoculture is free from worry about another worm- or virus-induced network meltdown? Of course not. And why not? Why, it’s because these same IT cowards leaders think such meltdowns are inevitable.
The inevitability of this century’s computer virus outbreaks is one of the implicit myths about their origin:
“Why switch to another operating system, since all operating systems are equally vulnerable? As soon as the alternative OS becomes dominant, viruses geared to that OS will simply return, and we’ll have to fight all over again in an unknown environment.”
My hope is that if you’ve been following my argument thus far, you now realize that this type of attitude is baseless, and simply an excuse to maintain the status quo.
Indeed, the same IT cowards leaders who actually believe this are feeding Microsoft propaganda about computer security to their frightened and techno-ignorant employees through “security awareness” courses such as this. Keep in mind that, as some of the notions point out, companies attempting to train their employees in computer security are doing so not only for their office PC, but for their home PC as well. The rise of telecommuting, another social upheaval caused by the Internet’s easy availability, means that the two are often the same nowadays. So the lessons American workers are learning are true only if they have Windows computers at home, and only if Windows computers are an inevitable and immutable technology in the corporate landscape, like desks and chairs.
Here are some of the things I learned from my organization’s “Computer Security Awareness” class:
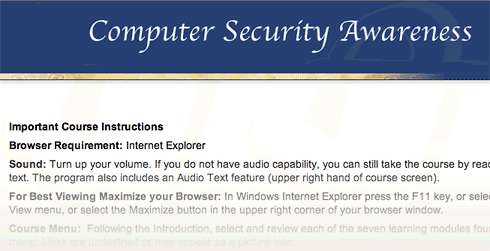
This computer security online training requires Internet Explorer.
This computer security online training requires Microsoft Internet Explorer.
- Always use Internet Explorer when browsing the web.
How many times must employees beg their companies to use Firefox, merely because it’s faster and has better features, before they will listen? In the meantime, to ensure that as many viruses and worms can enter the organization as possible, so that the expensive antivirus software we’ve purchased has something to do, IT management makes sure that as many people continue using IE as possible. I’m being facetious here. The reason they do this is that it’s what the training vendor told them to say, and today’s Federal IT managers always do as instructed by their contractors.While you can find data on the web to support the view that IE is at least as secure as Firefox, common sense should guide your decisionmaking here rather than the questionable advice of dueling experts. The presence of Active/X in IE, all by itself, should be enough to make anyone in charge of an organization’s security jump up and down to keep IE from being the default browser. And that’s not even usually listed as a vulnerability, because it’s no longer “new”.
The “shootouts” that you read now and then pertain to new vulnerabilities that are found, and to the tally of vulnerabilities a given browser maker has “fixed”… not to inherent architectural vulnerabilities like Active/X and JScript (Microsoft’s proprietary extension to JavaScript).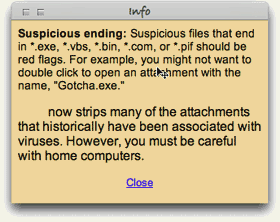
Students learned to fear the kinds of files Windows users exchange on a day-to-day basis.
Students learned to fear the kinds of files Windows users exchange on a day-to-day basis.
- Use Windows computers at home.
The belief among IT management in recent years is that if we can get everyone to use the same desktop “image” at work and at home, we can control the configuration and everything will be better. Um, no. Mac users don’t have any fear of these strange Windows file types, and organizations that encourage users to switch to Mac OS X or to Linux, instead of discouraging such switching, immediately improve their security posture. For example, here’s some recent advice from a security expert at Sophos:
“It seems likely that Macs will continue to be the safer place for computer users for some time to come.”
And from a top expert at Symantec comes this recent news:
Simply put, at the time of writing this article, there are no file-infecting viruses that can infect Mac OS X… From the 30,000 foot viewpoint of the current security landscape, … Mac OS X security threats are almost completely lost in the shadows cast by the rocky security mountains of other platforms.
- All computers on the Internet can be infected within 30 minutes if not protected.
No… of all currently available operating systems, this is true only of Microsoft Windows. Mac OS X is an example of a Unix system that’s been designed to use the best security features of the Unix platform by default, and no user action or configuration is required to ensure this.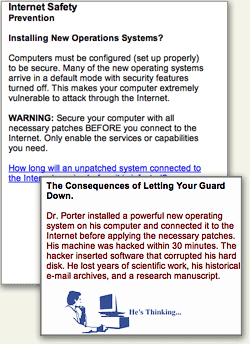
The course taught us that all computers need to be "configured" to be secure and that otherwise, they would be infected by a virus in 30 minutes on the web.
The course taught us that all computers need to be "configured" to be secure and that otherwise, they would be infected by a virus in 30 minutes on the web.
Here’s one of the URL’s (from the SANS Institute) that the course provided, which actually makes pretty clear that Windows systems are the most insecure computers you can give your employees today: Computer Survival History. - Spyware is a problem for all computers.
I imagine that spyware is the most cripplingday-to-day aspect of using Windows. My son insisted on trying Virtual PC a couple of years ago, and on his own, his virtual Windows XP was completely unusable because of malware of various kinds within about 20 minutes. He was using Internet Explorer, of course, because that’s what he had on his computer. I installed Firefox for him, and his web surfing in Windows has been much smoother since then. He still has to run antivirus and antiadware software to keep the place “clean,” but needless to say, he has never asked to use IE again. This experience alone demonstrated what I had already read to be true: The web is not a safe place in the 21st century if you’re using Windows. This is one of the primary reasons I use Mac OS X: In all the 5 years I’ve used Mac OS X, I have never once encountered adware. And that has absolutely nothing to do with what websites I surf, or don’t surf, on the web. (And that’s all I’m going to say about it!)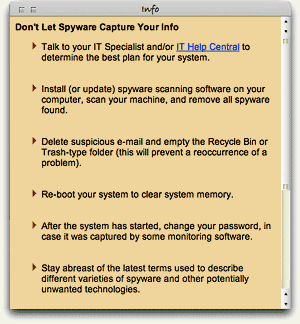
These instructions on viruses assume that the employee runs Windows at home.
These instructions on viruses assume that the employee runs Windows at home.
- Viruses are a threat to all home computers.
What I said previously about adware,ditto for computer viruses. To this day, there is not a single virus that has successfully infected a Mac OS X machine. (The one you heard about earlier this year was a worm, not a virus, and it only affected a handful of Macs, doing very little damage in any case.) As even Apple will warn you, that doesn’t mean it’s impossible and will never happen. However, it does mean that if Macs rise up and take over the world, amateur virus writers will all have to retire, and you’ll cut the supply line of new virus hackers to the bone. Without Windows to hack, it simply won’t be fun anymore. No quick kills. No instant wins. Creating a successful virus for Mac OS X will take years, not days. Human nature being what it is, I just know there aren’t many hackers who would have the patience for that.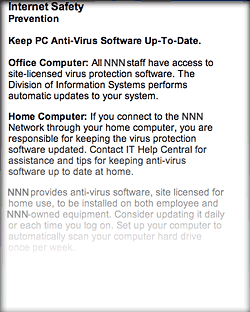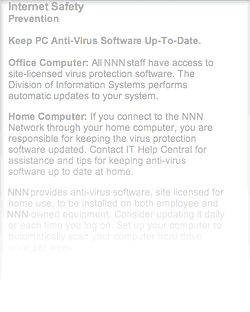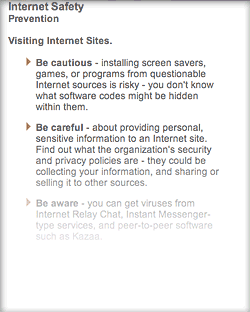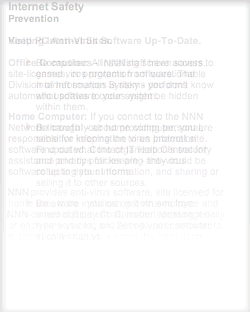
The course taught me to be afraid and wary when using the Internet at home.
The course taught me to be afraid and wary when using the Internet at home.
A huge side benefit for Mac users in not having to worry about viruses and worms is that you don’t have to run CPU-sucking antivirus software constantly. Scheduling it to run once a week wouldn’t be a bad idea, but you can do that when you’re sleeping and not have to suffer the annoying slowdowns that are a fact of PC users’ lives every time those antivirus hordes sally forth to fight the evil intruders. Or… you could disconnect your Windows PC from the Internet, and then you could turn that antivirus/antispyware thingy off for good.
- Malicious email attachments are a threat to all.
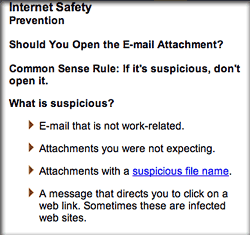
Apparently, you have to be really careful when opening email attachments, since they might attack your computer.
Apparently, you have to be really careful when opening email attachments, since they might attack your computer.
**Y A W N** Can we go home now?
Sometimes, I open evil Windows attachments just for the fun of it… to show that I can do so with impunity. Then I send them on to the Help Desk to study.:-) (Just kidding.)
Change resisters in charge
Other than Microsoft, why would anyone with a degree in computer science or otherwise holding the keys to a company’s IT resources want to promulgate such tales and ignore the truth behind the virus plague? That’s a simple one: They fear change.
To admit that Windows is fundamentally flawed and needs to be replaced or phased out in an organization is to face the gargantuan task of transitioning a company’s user base from one OS to another. In most companies, this has never been done, except to exorcise the stubborn Mac population. Although its operating system is to blame for the millions of dollars a company typically has had to spend in the name of IT security over the last 5 years, Microsoft represents a big security blanket for the IT managers and executives who must make that decision. Windows means the status quo… it means “business as usual”… it means understood support contracts and costs. All of these things are comforting to the typical IT exec, who would rather spend huge amounts of his organization’s money and endure sleepless nights worrying about the next virus outbreak than to seriously investigate the alternatives.
 Managers like this, who have a vested interest in protecting Microsoft’s monopoly, are the main source of the Windows security myths, and it’s a very expensive National embarrassment. The IT organization is simply no place for people who resist change, because change is the very essence of IT. And yet, the very nature of IT operations management has ensured that change-resisters predominate.
Managers like this, who have a vested interest in protecting Microsoft’s monopoly, are the main source of the Windows security myths, and it’s a very expensive National embarrassment. The IT organization is simply no place for people who resist change, because change is the very essence of IT. And yet, the very nature of IT operations management has ensured that change-resisters predominate.
Note that I said IT operations. As a subject for a future article, I would very much like to elaborate on my increasingly firm belief that IT management should never be handed to the IT segment that’s responsible for operations—for “keeping the trains running.” Operations is an activity that likes routines, well defined processes, and known components. People who like operations work have a fondness for standard procedures. They like to know exactly which steps to take in a given situation, and they prefer that those steps be written down and well-thumbed.
By contrast, the developer side of the IT organization is where new ideas originate, where change is welcomed, where innovation occurs. Both sides of the operation are needed, but all too often the purse strings and decisionmaking reside with the operations group, which is always going to resist the new ideas generated by the other guys. In this particular situation, solutions can only come from the developer mindset, and organizations need to learn how to let the developer’s voice be heard above the fearful, warning voices of Operations.
Custer’s last stand… again
So please, Mr. or Ms. CIO, no more silly security training that teaches me how to [try to] keep secure an operating system I don’t use, one that I don’t want to use, and one that I wish to hell my organization wouldn’t use. Please don’t waste any more precious IT resources spreading myths about computer security to my fellow staffers, all the while ignoring every piece of advice you receive on how to make fundamental improvements to our network and desktop security, just because the advice contradicts what you “already know.”
It really is true that switching from Windows to a Unix-based OS will make our computers and network more secure. I recommend switching to Mac OS X only because it’s got the best designed, most usable interface to the complex and powerful computing platform that lies beneath its attractive surface. Hopefully, Linux variants like Ubuntu will continue to thrive and provide Apple a run for its money. The world would be a much safer place if the cowards leaders who make decisions about our computing desktop would wake up, get their heads out of the sand, smell the roses, and see Microsoft Windows for what it is: The worst thing to happen to computing since… well, … since ever!
 Before my recommendation is distorted beyond recognition, let me make clear that I don’t advocate ripping out all the Windows desktops in your company and replacing them with Macs. Although that’s an end-point that here, today seems like a worthy goal, it would be too disruptive to force users to switch, and you’d just end up with the kind of resentment that the Macintosh purges left behind as the 1990’s ended. Instead, I’ve always recommended a sane, transitional approach, such as this one from my November 2002 paper on the subject (note that names have been changed to protect the guilty):
Before my recommendation is distorted beyond recognition, let me make clear that I don’t advocate ripping out all the Windows desktops in your company and replacing them with Macs. Although that’s an end-point that here, today seems like a worthy goal, it would be too disruptive to force users to switch, and you’d just end up with the kind of resentment that the Macintosh purges left behind as the 1990’s ended. Instead, I’ve always recommended a sane, transitional approach, such as this one from my November 2002 paper on the subject (note that names have been changed to protect the guilty):
Allow employees to choose a Macintosh for desktop computing at NNN. This option is particularly important for employees who come to NNN from an environment where Macintoshes are currently supported, as they typically are in academia. In an ideal environment, DITS would offer Macintoshes (I would recommend the flat-panel iMacs) as one of the options for desktop support at NNN. These users can perform all necessary functions for working at NNN without a Windows PC.
This approach simply opens the door to allow employees who want to use Macs to do so without feeling like pariah or second-class citizens.
As long ago as 2002, Mac OS X was able to navigate a Windows network with ease, and assuming your company already has a Citrix server in place, Mac users can access your legacy Windows client-server apps just as well as Windows clients can. This strategy will gradually lower security costs—and probably support costs as well—as the ratio of Windows PCs to Macs in your organization goes down, while lowering the risk of successful malware attacks. As a side benefit, I would expect this strategy to improve user satisfaction as well. Since the cost of Apple desktops today is roughly the same as big-brand PCs like Dell, the ongoing operational cost of buying new and replacement machines wouldn’t take a hit, as the IT mythmakers would have you believe. In fact, did you know that all new Apple computers come with built-in support for grid computing? Certainly! Flick a switch, and your organization can tap into all the Mac desktops you own to supplement the company’s gross computing power. What’s not to like? (My 2002 report didn’t cover grid computing — it was a new feature in Mac OS X 10.4 last year — but it did address all the issues, pros, and cons an organization would face in integrating Macs with PCs; however, it’s too large a subject to discuss further here.)
But how do you convince IT managers of this, when operating systems from Microsoft are the only kind they’ve ever known? I certainly had no luck with mine. Heck, I didn’t even gain an audience to discuss it, and my fellow mid-level IT managers were aghast that I had even broached the subject. After all, many of them were still smarting from the bruising—but successful—war against Mac users they had waged during 1994-96. The fact that in the meantime Apple had completely rewritten its operating system, abandoning the largely proprietary one it built for the original Macintosh and building a new, much more powerful one on top of the secure and open foundation of Unix made no difference to these folks whatsoever. It’s not that they disagreed with any of the points I was trying to make… they didn’t even want to hear the points in the first place!
A new approach for IT managers
 For the most part, the managers who, like “hear no evil” chimps, muffled their ears back in 2002 were in charge of IT operations. To them, change itself is evil, and the thought of changing your decision of 5 years ago for any reason was simply unthinkable. And yet… consider how much the computer landscape changes in a single year nowadays, let alone in 5 years. Individuals with good technical skills for operations management but no tolerance for change should simply not be allowed to participate in decisions that require objective analysis of the alternatives to current practice. And at the pace of change in today’s technology market, inquiry into alternatives needs to become an embedded component of IT management.
For the most part, the managers who, like “hear no evil” chimps, muffled their ears back in 2002 were in charge of IT operations. To them, change itself is evil, and the thought of changing your decision of 5 years ago for any reason was simply unthinkable. And yet… consider how much the computer landscape changes in a single year nowadays, let alone in 5 years. Individuals with good technical skills for operations management but no tolerance for change should simply not be allowed to participate in decisions that require objective analysis of the alternatives to current practice. And at the pace of change in today’s technology market, inquiry into alternatives needs to become an embedded component of IT management.
For what it’s worth, here are a few principles from the Martian Code of Conduct for IT management:
- Make decisions, and make them quickly.
- Decisions should always consider your escape route in case you make a bad choice
- Escape routes should enable quick recovery with as little disruption to users as possible
- Open source options should always be considered along with commercial ones.
- COTS doesn’t stand for “Choose Only The Software” Microsoft makes.
- Sometimes it’s better to build than to buy. Sometimes it’s better to buy than to build. A wise IT manager knows the difference.
- Reevaluate your decisions every year, to determine if improvements can be made.
- Don’t cling to past decisions just because they were yours.
- Never lock yourself in to one vendor’s solution. Always have an escape route. (Wait… I said that already, didn’t I?)
- Know thy enemy. Or at least know thy vendor’s enemy.
- Be prepared to throw out facts you’ve learned if new information proves them wrong.
- IT is a service function, not a police function. Remember that the purpose of the IT group is to skillfully deploy the power of information technology to improve productivity, communictions, and information management at your organization.
- Never let contractors make strategic IT decisions for your company.
- Never take the recommendation of a contractor who stands to gain if you do. (In other fields, this is called “conflict of interest.” In some IT shops I know, it’s called “standard practice.”)
- Don’t be afraid to consider new products and services. When you reject a technology or tool a customer inquires about, be sure you understand why, and be prepared to explain the pros and cons of that particular technology or tool in language the customer will understand.
- Make sure your IT organization has components to manage the following two primary activities on an ongoing basis, each of which has its requirements at the table when you compile budget requests for a given year:
- Application developers capable of handling a multitude of RAD tasks. This group should maintain an up-to-date laboratory where new technology and tools can be evaluated quickly.
- Operations group with subcomponents for dealing with networking, telecommunications, desktop management, security, data, and application/server maintenance.
- Always obtain independent estimates of whatever resource requirements the operations group tells you are needed to make significant changes in technology platforms at your organization, because an operations manager will always exaggerate the true costs.
- The success of your organization is measured not by the size of the desktop support group’s Help Desk, but rather by continued progress in reducing the number of requests and complaints that are referred to the Help Desk. A rise in Help Desk requests over time is a symptom that something is probably wrong—not a signal to ask for a larger Help Desk budget.
- Similarly, the percentage of a company’s budget that gets devoted to IT should become smaller over time if the IT group is successfully discharging its mission. Calls for larger IT budgets should be viewed skeptically by the COO, since it often symptomizes an IT group that is unable or unwilling to find better alternatives to current practice.
From the perspective of an IT manager who has never worked with anything but Windows desktops, the prospect of having to welcome Macintosh or Linux systems into your Windows-only network must be a frightening one indeed. If you know absolutely nothing about Mac OS X and your only experience with a Mac was a brief hour or two with OS 7 a decade ago, your brain will very likely shut down at such a thought, and your hands will plant themselves on your ears if a colleague begins speaking in that direction. This is entirely understandable, and it’s equally understandable that the vast majority of your existing Windows users will want to remain on the only computing platform they’ve ever known.
But don’t you see that this fear doesn’t mean a decision to support Mac OS X in your organization is wrong! Such fears should certainly be considered in a transition plan, but they shouldn’t be considered as a reason to oppose development of a transition plan. Fears like these, and the sometimes irrational attitudes they bring to bear in technology decisionmaking, is why we desperately need new blood in the Nation’s IT departments, and why applicants to the job whose only (or only recent) training has been in MCSE shops should be filtered out from the get-go. You often hear Macintosh users “accused” of being cultish, but from my perspective, steadfast Microsoft Windows partisans are much more likely to meet the following definition of “cultish” than the Mac users I’ve known:
A misplaced or excessive admiration for a particular person or thing.
By fostering the myths about malware threats, the cult of Microsoft has already poisoned the computing experience for millions of people and wasted billions of dollars trying to shore up the bad past decisions of its Microsoft-trained hordes.
It’s time to give some new ideas a shot. It’s time to begin a migration off of the Microsoft Windows platform in U.S. corporate and government offices. Only once we dismantle the Microsoft computing monoculture will we begin to beat back the malware plague. Until then, IT security will simply spin its wheels, implement security policies that punish the whole software development life cycle because of Microsoft’s sins, ![]() and require Mac OS X users to take online security training that simply teaches all the things we have to fear from using Windows computers.
and require Mac OS X users to take online security training that simply teaches all the things we have to fear from using Windows computers.
Addendum: A few articles for further reading:
Colophon
This article is the first time I’ve used a new, very useful JavaScript called Image Caption from the Arc90 lab site. Image Caption makes it easy to include text captions with the graphics you publish to illustrate your text. It includes a small JavaScript file and some sample CSS code. To implement, you simply add a class attribute to the images you want to caption, add the caption text as a “title” attribute, and include the script in the head of your HTML code.
I also had fun using the terrific JavaScript called simply Reflection.js. It’s recently shed about 30kb of file size and is down to only about 5kb, works great alongside Prototype/Script.aculo.us, and is childishly simple to execute. Besides adding a link to the JavaScript file, you add a class attribute to the images you want to reflect. For each reflection, you can tweak the reflection height and its opacity by adding specific measures in two additional class attributes. Unlike other reflection scripts I’ve tried, this one automatically reflows the text once the reflected image is added to the layout.
PC World Offers Advice on Improving Microsoft
Apple Market Share Myths Exposed!
The Apple Market Share Myth
MacDailyNews Doesn’t Mourn Bill Gates (Neither Do I)
Video Shows John Dvorak Explaining How He Lies To Get Hits
Yahoo’s Ajax/DHTML User Interface Library Apparently Fails Its Own Test
I have been among the developers and observers who have praised Yahoo for the technical strength of their recently launched User Interface Library. In my tests for the Ajax/DHTML Scorecard project in March, Yahoo’s library was a clear “A” in its cross-browser credentials, and I was very impressed with Yahoo’s development team, which published clear and exacting browser standards for their library.
According to Yahoo’s own Graded Browser Support table, Safari is an A-graded browser, meaning it achieves the highest level of support possible with the Yahoo interface library. Clearly, the thought that went into this table is impressive, and the authors conclude the explanation that precedes the table itself with an appropriate quote from Tim Berners-Lee on the importance of cross-browser support:
“Anyone who slaps a ‘this page is best viewed with Browser X’ label on a Web page appears to be yearning for the bad old days, before the Web, when you had very little chance of reading a document written on another computer, another word processor, or another network.â€
It is therefore highly disappointing and disillusioning to discover tonight that Yahoo has released a preview of its new, Ajax-enabled home page with support only for Internet Explorer 6.0 and Firefox 1.5. The only logic one can use to justify such a move is based on a totally PC-centric viewpoint, which argues that only Windows users are worth troubling with, since they comprise the vast majority of potential viewers. But this is precisely the viewpoint that must cease if Web 2.0 is to become the fertile melting ground for truly cross-platform interdependence that it wants to be. It’s simply not the viewpoint of any company that really cares about Berners-Lee’s vision or about the millions of users on platforms other than the virus- and malware-riddled mess that is Microsoft Windows today.
Web 2.0 sites should be built to open standards, and any catering to specific browser extensions should be avoided. If proprietary extensions are utilized, they should have no effect on the site’s core functionality, and should not be even noticed by users of other browsers. For example, I’ve employed a harmless extension to the HTML text input field that Apple developed in order to beautify search forms in Safari. It’s nice for Safari users, but has no impact on IE users or on Firefox users on any platform.
From my experience working with Ajax and DHTML in 2006, I am certain that Internet Explorer was the hardest browser for Yahoo to support in terms of time and resources. No doubt the rollout of this new home page had to wait until it worked well enough in IE. What boggles my mind is that if you can support Firefox, there’s no earthly reason why you shouldn’t also be able to support Opera 9.0 and WebKit (Safari). (OK, you might have to make a few very minor tweaks, but nothing too challenging for a reasonably skilled CSS/JavaScript guru.)
Does this mean that the Yahoo Interface Library isn’t as truly cross-browser as Yahoo claims? Does it mean that Yahoo is blatantly disregarding its own graded browser support standards?
In answer to the first question, “Who knows?” All I know is, the new site doesn’t work in Safari or Opera. And that’s just plain wrong. Using a modern JavaScript library, it’s much easier to build an Ajax/DHTML Web 2.0 site that supports Firefox, Opera, and Safari, all of which have A+ compliance with w3c standard, and then figure out what hacks you need to use to get the site to work in IE 6.0. To do the work backwards starting with IE 6.0 simply exaggerates that browser’s importance to the future of the web. If Yahoo used their own JavaScript library to build their new home page, it doesn’t speak very highly of that toolkit’s abilities.
In answer to the second question, the answer is clearly, “Yes!” Yahoo has blatantly disregarded its own published standards for browser support in 2006.
Yahoo, I’m extremely disappointed, and I’m sure others will be, too. If nothing else, this will push back to a much lower priority my plan to rebuild a number of the Ajax/DHTML functions of Musings from Mars using Yahoo’s library… simply for comparison purposes. Now, I’m definitely going to make Dojo the next library on my list… especially now that they have that spiffy new home page design, which I can actually use in Safari. (Imagine that!)
Mossberg Sees Apple’s “Device Model” Gaining Respect
Is It Possible This Reuters Writer Can’t Read? Nah!
While reading MacDailyNews this evening, I happened on a remarkable story entitled, “Another iPod+iTunes FUD article keeps the disinformation flowing.” With a sigh, I took a look to see what idiot could possibly not understand the iPod and/or iTunes after so many years and so many articles.
As it turned out, the depth of this writer’s ignorance is absolutely shocking. There’s no way he could honestly think this stuff is true. If he does, he has no business covering complicated (yeah, right!) technology topics like the iPod and iTunes, because clearly the product’s available options are far too difficult for him to grasp. Concluding instead that he’s probably a bright guy, I’m tempted to infer, as MacDailyNews did, that his piece in Reuters is a deliberate attempt to mislead consumers and smear Apple’s innovative and highly successful music service. The article appears as part of Yahoo’s Finance site with the innocuous-sounding title “Do you own songs bought online? Well, sort of“.
After reading just the first few paragraphs, I whipped out my fingers and dashed off a letter using the Yahoo site’s contact form, which says “Our editors are interested in your comments. Please send us your feedback on Reuters news or photos.” Not being a shy guy in a case like this, that was all the encouragement I needed.
Hello,
A friend told me of an article on your website today… written by someone named Duncan Martell. This person should be fired for ignorant, irresponsible journalism. I didn’t bother to read the whole article, because there were so many patent untruths in the first few paragraphs.
To mention just two:
- “Apple’s FairPlay… prevents you from listening to those purchased songs on a music player from Dell, Creative, Sony, …” This is b*llsh*t. All you have to do is burn the songs to a CD, and you can then import them to whatever player you’d like to use them on. All the author of this article is doing is spreading malicious misinformation. Clearly, he has a beef of some kind against Apple or the iPod, and his bias is showing. By bias, I mean ignorant prejudice about something he doesn’t fully understand.
- “The same goes for songs you’ve imported to your computer from CDs you already own.” This is an absolute lie, no way to read it otherwise. You can import music from CDs into iTunes in a half a dozen different formats that are all industry standards with no Digital Rights Management attached to them at all. As I said, you should fire Mr. Martell, or make sure he never covers another technology topic, because this statement is outrageously false. When you put a CD into your computer, you can import into iTunes in the following totally open and freely transferrable formats: MP3, WAV, AIFF, AAC (MP4). MP3 and AAC are industry standard, nonproprietary compressed audio formats, and you can freely convert back and forth between these in iTunes if you change your mind later. WAV and AIFF are industry standard non-compressed formats that are the formats used on CDs themselves.
The credibility of your organization’s news and technology coverage is severely compromised by writers like Duncan Martell, who, in trying to make a possibly legitimate point about DRM (which by the way applies to Microsoft’s DRM format as well), stretches the truth in one case and totally obliterates it in the other. Not bothering to read the rest of his “article,” I don’t know how many more factual errors he made.
I would also seriously recommend firing the editor in charge, who should have demanded fact checking before publishing this.
Regards,
Leland Scott
Will ignorant press about the iPod/iTunes never cease? Frankly, not until Microsoft gives up in its effort to break into that market with its inferior Windows Media Player-based solution.
It’s difficult to think of another industry where unethical tactics like this are regularly employed. Can you imagine the president of GM saying something like, “Did you know that Ford makes engines that can only be used in other Ford vehicles? It’s true… Buy a Ford, and you’re stuck with it for life.” I mean, huh?
Ever since Microsoft began its run at monopoly in the early 1980’s, the computer industry has become accustomed to truth being a shade of grey, and product announcements being considered an opportunity to tell Really Big Lies about possible future products. Look at Vista, for god’s sake. They’ve been talking that one up since June 2001! If you think I’m exaggerating, check out “Mr. Microsoft’s” (Paul Thurrott) website, the Win Supersite, to check.
You know, one of the reasons the good guys always lose the first battle or two in movies and books is that, unlike the bad guys, they aren’t willing to lie or cheat in fighting the war. The bad guy, of course–it’s part of what makes him so bad–will do anything to win, and hesitates not to pull a dirty trick or three in that effort. Tactics like what Microsoft has been doing for 15 years–lying about its adversaries, exaggerating features of its software products, announcing products that don’t exist in order to ward off competition, to name a few of the least serious ones–are clearly “bad guy” tactics.
And I think we all know what happens to the bad guys at the end of the picture, don’t we? As the end of the picture approaches, and as the good guys are finally making headway against all odds, don’t be at all surprised to see the intensity of nastiness in the PC industry ratchet up a notch or two.
Dave Winer Has Been Bad Again, and Les Posen’s Hunting Him Down!
Latest Consumer Reports Survey Still Finds Apple Tops in Customer Support
MacDailyNews: A Banner Day for Anti-Apple FUD
Dvorak Sees Eight Bad Signs for His Former Favorite Company
At PC Magazine, Writing About the Mac With PC Blinders On
MacDailyNews reports on yet another bull-headed article that appears in PC Magazine spreading anti-Mac propaganda to anyone who will listen. The equally bull-headed MacDailyNews reporter proceeds to begin tearing the author to little bits, as he had already done with a PC Mag story by the same author a few days earlier.
Sure enough, PC Mag’s Michael Miller has written what I’m sure he believes is a reasonable comparison of the state of things with Mac OS X versus Windows. What he doesn’t realize is that he’s full of B***hit, ensnared in a system he thinks he understands but is really merely apologizing for. In doing so, he adheres to old Mac myths that he’ll probably believe till he steps over that final cliff.
Miller tries once again to make the case that Macs are more expensive than PC’s and that they don’t have enough software. If I weren’t so irritated by this, I’d simply yawn. In one case, he writes of visiting the Dell store and buying an E1505 notebook for only about $1,300, while the entry-level MacBook Pro with roughly the same specs is $1,999.
I have no idea how he got to that price, because I just visited, and without loading the Dell up with enough software to even come close to what the Mac offers, and taking advantage of a time-limited $200-off coupon, that E1505 cost me $1700. That’s still less than the MacBook, but then it’s heavier, larger, has less software, has no webcam, has very little useful software, and only runs Windows XP media center (no TV tuner, folks). (See this PDF file to review my bill.)
To refute this guy’s argument point by point would take more time than I’ve got, but I do intend to write an article about the Mac software market soon and will invite him to read it. Mac software is so far ahead of Windows it’s not even funny. Ever heard of “quality, not quantity?” Mr. Miller? PC’s definitely have quantity, I’ll give them that if they really want it. But we’ve got the quality market all sewn up!
And, as I’ll report, there’s way too much great Mac software these days if you’re actually trying to follow the market and catch all the cool developments. Perhaps if Mr. Miller spent a few days on his Mac trying out all the new releases that come out for Mac OS X on MacUpdate and VersionTracker, as well as the Dashboard Widget market, he’d get a new perspective on that part of his argument.